
These assessments allow businesses to make more informed decisions and drive revenue growth. The point of sale (POS) industry is no exception.
Today’s POS systems collect huge amounts of data, including sensitive customer data. That data must be safeguarded by top data security protocols and procedures.
Consumers have concerns and need reassurance that their data is being protected.
When it comes to protecting your business, especially when data is involved, you need to take every precaution possible. This means you should have regular security assessments done by a company that specializes in cyber security. Security assessments identify vulnerabilities that criminals could exploit to attack your company’s systems and data, as well as help you develop contingency plans to deal with any attacks or disasters that may occur. A security assessment is a detailed review of all systems and networks, including physical and virtual components within your company’s infrastructure. These assessments cover everything from data access controls and authentication protocols to software patch levels and aging hardware. They also provide a prioritized list of gaps, with a plan for how to fill those gaps. This helps your IT team create realistic budgets for future security expenses, and it also allows you to build a strong culture of cybersecurity awareness amongst employees. The Importance of a Security Assessment also helps you meet compliance requirements for regulatory bodies, such as HIPAA for healthcare companies or PCI DSS for retail businesses. It is not enough to simply comply with these regulations, you need to show that you are working hard to prevent breaches and attacks from occurring in the first place. A security assessment provides the documentation you need to demonstrate that your business is making these efforts. This will not only protect you from fines and penalties, but it will also protect your customers’ data as well.
They ask themselves questions like:
- How safe is the personal data I give to companies I do business with?
- Can unknown third-party entities access my data?
- How easily could hackers access the data stored by vendors I purchase from?
- Are the systems those businesses use prone to viruses that could make my data vulnerable?
These are important questions that align with common concerns consumers have in today’s digital, data-driven world.
What Is It Important to Conduct a Security Assessment?

This requires carrying out a data security risk assessment, complying with the latest data security protocols, and becoming certified by the highest industry standards of data protection.
But how do you perform a security assessment? Do you need a security risk assessment tool? Or a special cyber security risk assessment template? How do you even begin?
Below we’ll dig into this topic and unpack important information that any business storing customer data need to know and understand.
Then we’ll touch on benefits and other important points to keep in mind when conducting a data security risk assessment.
First, we’ll start with some basics for those starting to learn about data security, and a refresher for those already knowledgeable about the subject.
What Is a Security Risk Assessment?
Also known as a cyber security risk assessment or an IT security risk assessment, it is essentially what it sounds like. It’s an audit of the systems you store data in, and the security measures you have in place to protect that data.
This audit generates a security risk assessment report that analyses your business’s data security preparedness and how secure your customer data actually is.
Common assessments evaluate how vulnerable your information technology (IT) solutions and internal operating processes are. They also provide informed recommendations for improvements in your security practices.
The end results is maximum insight into how secure your data is and which measures will reduce its vulnerability.
Why Are Security Risk Assessments So Important?

In an age where a single cyberattack can spell financial ruin for any company, the importance of security risk assessment is more important than ever. Whether due to regulatory requirements aimed at protecting sensitive information or the desire to keep customers and business partners happy, companies of all sizes must invest time, resources and money into assessing and mitigating their risk. To be effective, any security risk assessment must identify and understand all the assets within an organization. This means generating a map of all hardware, applications and data storage containers that might be vulnerable to attack. Once an asset map is established, it is possible to determine how a specific threat would impact each asset and the likelihood of occurrence. Then, it becomes a matter of prioritizing the most valuable assets to protect first. Trade secrets, user data and intellectual property take precedence over the cost of restoring primary business functions after an attack. Lastly, the assessment must evaluate and score the company’s protocols in comparison to recognized standards. This is particularly true for industries like healthcare, which are required to reveal their storage and data sharing practices in order to meet government regulations such as HIPAA. A security risk assessment can help a company remain compliant with these regulatory frameworks, as well as create transparency and trust in the minds of the company’s clients, customers and partners. It is a crucial tool for any business that must balance the need to protect its brand image and personal information with the need to keep the company’s systems running efficiently.
Proving to your customers that you are certified by the most stringent data security protocols is critical to building trust in your brand.
If prospects are not convinced that their data will be 100% secure, they are far less likely to do business with you.
Plus, if you do experience a data breach, it can have devastating impacts on your business. It can, in fact, mean the end of your business.
Unfortunately, smaller businesses suffer the most from data hacks and breaches.
Consider these statistics:
- 43% of data-related cyber attacks are targeted at small businesses (Source).
- 60% of small businesses that experience a cyber attack find themselves out of business within six months or less (Source)
Basic Cyber Attacks
You may already be familiar with the most basic types of cyber attacks. Here we cover the two most common types.
Malware Attacks
“Mal” means “bad” in Spanish. Tack on the end of the word “software” and you have “malware.”
The term malware refers to worms, viruses, spyware, and ransomware.
Malware is, in the most basic sense, bad software that installs itself or otherwise gains access to the data in an operating system. This generally happens when someone clicks an unknown, risky link in an email or downloads a dangerous attachment.
Clicking the link or opening the attachment sets in motion the installation of that “bad software” on your operating system. It takes place behind the scenes and is well masked, so you don’t notice.
Once installed, malware can:
- Obtain sensitive data from your database without your knowledge
- Prevent access from key processes and components of your operating system
- Interrupt the functioning of important components of your operating system, rendering it inoperable
Phishing Attacks

Their primary goal is to manipulate recipients into disclosing sensitive personal data such as credit card and login information.
Phishing attacks also, at times, install malware on the recipient’s operating system.
Advanced Cyber Attacks
More advanced cyber attacks are harder to detect and have more serious consequences when carried out successfully.
They can dig deeper into your database to uncover more secure data than basic attacks can. They use advanced masking techniques that allow the attacks to fly under the radar of many data security checkpoints, making them more dangerous and a greater risk.
This is why it’s quite important to understand the range of cyber attacks and put in place measures to catch them all, not just the basic ones.
The Benefits of Regular Assessments
Here are some key benefits:
- Identifying potential threats before they take place
- Spotting vulnerabilities in your security systems so you can resolve them before they are exploited
- Predicting the effects that specific, potential attacks could have on your business
- Providing cyber threat recovery options
- Increasing awareness of the types of attacks that pose the largest threat at any given time
- Taking actions ahead of time to prevent potential attacks
- Improving your brand reputation and reassuring prospects and customers that their data will be safe when they do business with your company
- Increasing compliance with payment card industry (PCI) data protection standards to provide peace of mind to customers performing online payments
In-House Vs. Outsourced Risk Assessments

Smaller businesses that don’t have the in-house capacity to conduct a security risk assessment often hire a third-party assessor to carry out the task. Doing so may seem more expensive than doing it in-house.
However, conducting your own security risk assessment in-house requires having a dedicated team on the payroll. So, at the end of the day, it may actually be cheaper to outsource.
Plus, many businesses that do assessments in-house can, at times, miss well-disguised threats. They then hire a third-party to do another assessment to ensure nothing was missed.
The route you take will depend on your budget and whether or not you keep an in-house security risk team on the payroll.
Recommended Best Practices
To cover every recommended practice around data security would require a separate article because the scope of that topic is so broad.
But here we share some of the key practices every business should keep in mind when developing a plan for protecting the data in their POS system.
Employee Data Security Training

These courses are generally taken online and educate employees on basic and more advanced tactics they can practice themselves to protect their data.
When selecting a training course, be sure to look for one that has been certified by top data security protocols.
Backing Up Your Data
These days most businesses conduct security risk assessments on cloud-based databases. This allows them to automatically back up data so that it is recoverable if it is stolen or otherwise destroyed or rendered inaccessible.
Backing up data is a must for businesses that use POS systems, and virtually every other type of business as well.
Strict Password Requirements
The more complicated a password is, the harder it is for hackers to identify it. That’s why it is important to implement stringent password requirements.
Common practices include requiring at least one capital letter, one number, and one non-alphanumeric symbol. It is also advisable to require users to create long passwords—eight characters at minimum.
Finally, businesses should require employees to change their login password every year at least, and every six months if possible. Plus, you should restrict the use of old passwords that employees have used in the past.
Limit User Privileges
POS systems give businesses the ability to determine the level of data access that each user has.
Some users may only be able to access certain functions but be restricted from others. That is necessary. If everyone had access to do everything in your system, chaos could ensue.
Set Up a Firewall

Any decent POS system should allow you to install virus protection software and a firewall if the system doesn’t already come with those things out of the box.
Conduct Assessments Often
Data security experts recommend that you conduct a security risk assessment once a month, or at least once per quarter.
Data management changes stemming from new projects have the capacity to render previously secure data processes insecure.
New threats pop up all the time so having a strict cadence around your security risk assessment is crucially important.
Additional Layers of Protection
Think of data protection measures like layers of an onion. The data is at the center but to get to it you must peel off various layers, each one being a little harder to peel.
Similarly, data protection should include multiple layers to minimize vulnerability. Below are a few additional layers of protection you can put in place to ensure your data is safer.
Renewing Employee Certification
Once an employee successfully completes a data security training course and becomes certified, they should retake the course every year. This helps employees to stay up to date on emerging threats and risks, and understand how to deal with them.
Physical Security Components
 A physical security risk assessment should be part of your overall assessment process.
A physical security risk assessment should be part of your overall assessment process.
It’s advisable to install a closed-circuit television (CCTV) monitoring system with cameras so you can check out what happened if a data breach occurs on site.
You should also include other basic physical security layers like coded locking systems to keep your business safe during closed hours.
If your data is highly sensitive, you can also employ guards, install fences, and leverage other practical security measures.
Data Encryption
Data encryption is a big one. The data passing from an employee into the POS system should be encrypted. And the data that passes from the system into the data server should also be encrypted.
User Roles
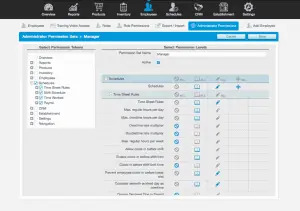 As mentioned above, it’s important to restrict the access each employee has to your data. You can do this by giving each user a “user role.”
As mentioned above, it’s important to restrict the access each employee has to your data. You can do this by giving each user a “user role.”
These can range from an “admin” user who has access to everything, to a “standard user” who can only see limited data.
Let’s use an example of a hypothetical situation a business could encounter during a risk assessment. A new employee starts her first day, and she is given access to all the data in the system.
Now she can see payroll information about her boss, revenue numbers, and other information that is above her paygrade.
Implementing user roles lets you limit access per employee based upon which data they need to access.
Wrapping It Up
Data security risk assessments are vital to the safety of your data. New strategies of attack are conceived in the minds of hackers every day.
It is important to stay ahead of those who would steal your and your customers’ data. By following the tips above you can ensure you have the right measures and processes in place to prevent attacks before they happen.
Plus, the advice outlined above will help you quickly resolve any data attacks that ever do happen.
The businesses that embrace data security risk assessments and put in place a strict data protection regime will be the ones that succeed today and in the future.
Those businesses that don’t take data security seriously and do not conduct data security risk assessments will be those who get hacked, lose customers, and ultimately fade from existence.

